Send and receive payments globally from anyone you can text for (basically) free
Download NowDownload
Sentz


Join us in the future of
cross-border payments

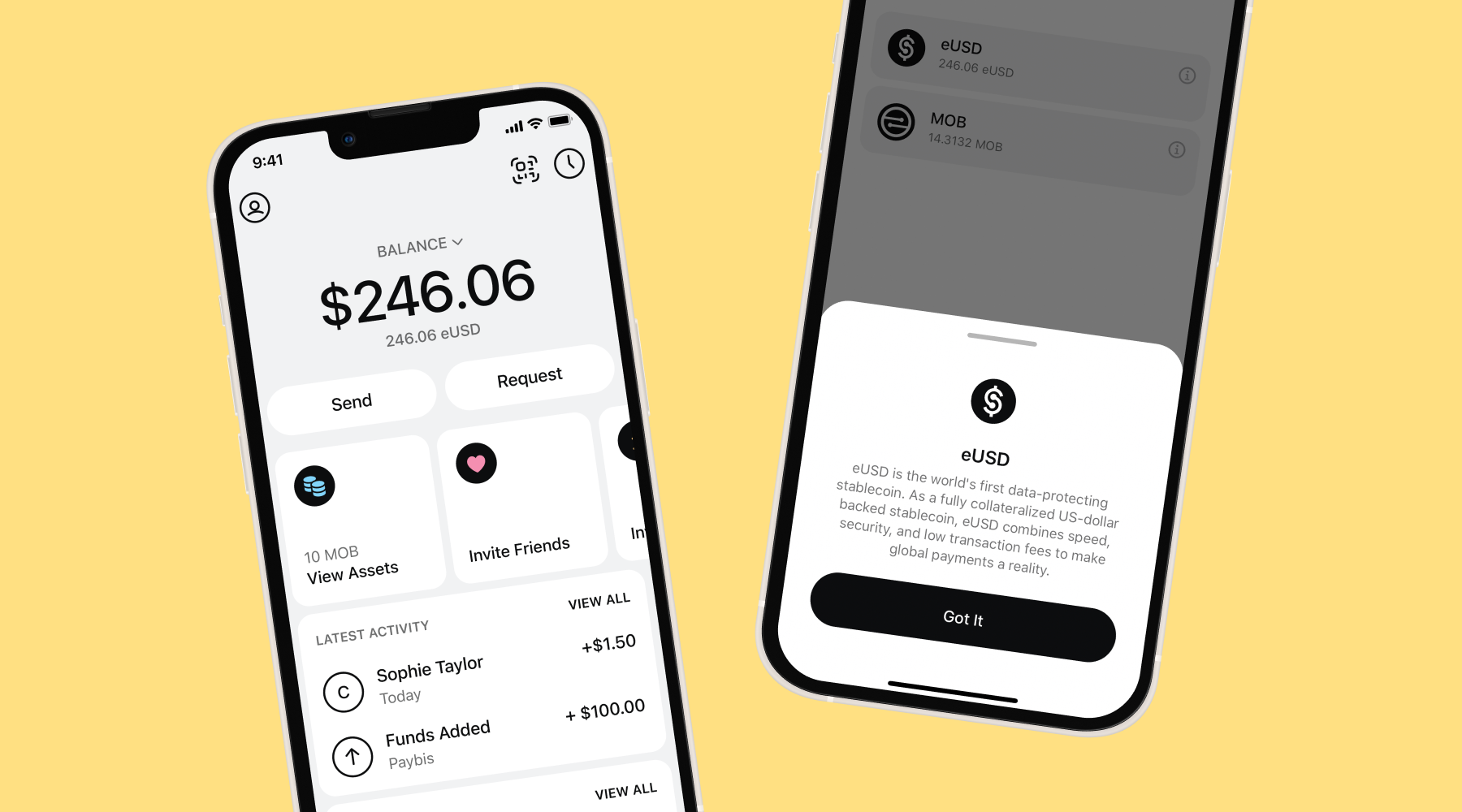
Instant Money
Transfer
Receive your money in
five seconds (or less!)

Basically
Free
Payments cost a
fraction of a cent

Simple &
Easy
Get paid with a phone
number - it's that easy

Easy as
Holding USD*
Withdraw instantly into your
local currency as needed

Reliable &
Secure
Encrypted payments -- only
share with trusted parties

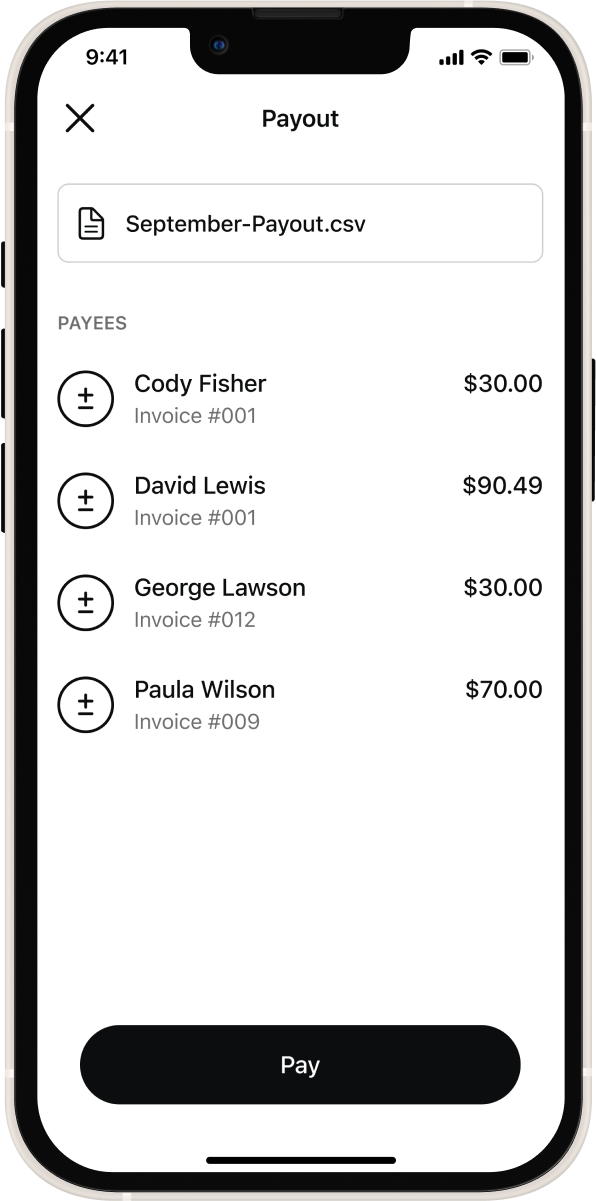
The easiest way to get paid as a freelancer
Why wait to get paid for your hard work? Sentz lets you get paid in seconds (versus days or weeks) from clients and businesses, no matter where they are in the world.
Freelancers Get Paid in Less Than 5 Seconds with Sentz
- Receive your payments in eUSD.
- Low transaction fees.
- Send invoices in seconds.
- Withdraw as USDT or USDC – bank withdrawals are coming soon to Nigeria!
The fastest and safest way to send payments
Sending payments to your friends and family globally shouldn't equal a headache.
Sentz is the fastest, easiest, most secure and inexpensive way to send money to friends and family in a different country.




International Payments for Businesses
Get in Touch